IPSEC VPN IKE实验

AR1配置如下:
[AR1]dis cu
#
sysname AR1
#
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255#
ipsec proposal p1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-cbc-256
dh group2
authentication-algorithm md5
#
ike peer R3 v2
pre-shared-key cipher %$%$}H”z!S,^u*;l(AQmOU4+,.2n%$%$
ike-proposal 1
local-address 12.1.1.1
remote-address 23.1.1.3
#
ipsec policy s1 10 isakmp
security acl 3000
ike-peer R3
proposal p1
#
interface GigabitEthernet0/0/0
ip address 192.168.1.254 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 12.1.1.1 255.255.255.0
ipsec policy s1
#
ip route-static 23.1.1.0 255.255.255.0 12.1.1.2
ip route-static 192.168.3.0 255.255.255.0 12.1.1.2
AR2配置如下:
[AR2]dis cu
#
sysname AR2
#
interface GigabitEthernet0/0/0
ip address 12.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 23.1.1.2 255.255.255.0
AR3配置如下:
[AR3]dis cu
#
sysname AR3
#
acl number 3000
rule 5 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
#
ipsec proposal p1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal 1
encryption-algorithm aes-cbc-256
dh group2
authentication-algorithm md5
#
ike peer R1 v2
pre-shared-key cipher %$%$}H”z!S,^u*;l(AQmOU4+,.2n%$%$
ike-proposal 1
local-address 23.1.1.3
remote-address 12.1.1.1
#
ipsec policy s3 10 isakmp
security acl 3000
ike-peer R1
proposal p1
#
interface GigabitEthernet0/0/0
ip address 23.1.1.3 255.255.255.0
ipsec policy s3
#
interface GigabitEthernet0/0/1
ip address 192.168.3.254 255.255.255.0
#
ip route-static 12.1.1.0 255.255.255.0 23.1.1.2
ip route-static 192.168.1.0 255.255.255.0 23.1.1.2
脚本如下:
1.R1与R3可以通信
2.匹配acl,定义需要ipsec保护的数据流
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
注意两端的acl源目相反。
3.配置ipsec 安全提议,定义保护方法
ipsec proposal p1 \\创建安全提议,名称p1
encapsulation-mode tunnel \\隧道模式封装新的ip头才能实现vpn功能
esp authentication-algorithm sha2-256 \\认证算法
esp encryption-algorithm aes-256 \\加密算法
4.配置ike协商和对等体
ike proposal 1 \\创建ike协商提议
encryption-algorithm aes-cbc-256 \\加密算法
dh group2 \\密钥交换算法
authentication-algorithm md5 \\认证算法
ike peer R3 v2 \\创建ike对等体,名称R3,版本2
pre-shared-key cipher huawei \\配置预共享密钥
ike-proposal 1 \\调用ike协商提议
local-address 12.1.1.1 \\本端地址
remote-address 23.1.1.3 \\对端地址
5.配置安全策略,调用acl和ipsec安全提议和ike对等体
ipsec policy s1 10 isakmp
security acl 3000 \\调用acl
ike-peer R3 \\调用ike对等体,完成密钥材料交换和对称密钥计算
proposal p1 \\调用IPSec安全提议
6.接口调用安全策略
interface GigabitEthernet0/0/1
ipsec policy s1
注意:R1和R3上需要有到达对端私网的路由,才能将流量从安全接口转发出去。
[AR1]ip route-static 192.168.3.0 24 12.1.1.2
[AR3]ip route-static 192.168.1.0 24 23.1.1.2
抓包分析:

验证现象:


 中型wlan部署有线和无线实验
中型wlan部署有线和无线实验 ospf的路由策略实验
ospf的路由策略实验 路由过滤与路由策略实验
路由过滤与路由策略实验 策略路由实验
策略路由实验 企业通过dhcp中继自动获取ip地址原理分析
企业通过dhcp中继自动获取ip地址原理分析 mpls部分php倒数第二跳抓包分析
mpls部分php倒数第二跳抓包分析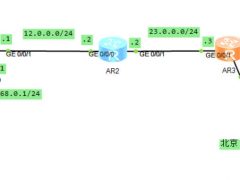 mpls vpn ldp动态lsp配置
mpls vpn ldp动态lsp配置 防火墙gre vpn隧道技术
防火墙gre vpn隧道技术